Denfotech Cyber Security Services

Corporate E-Crime Investigation
Our team of qualified digital forensics professionals is ready to assist or investigate any cybercrime and corporate e-crime related issues.
We investigate any illegal computer activity perpetuated by employees or cybercriminals, be it Illegal downloads suspicious network activity, slow network performance, documents forgery, detection of document alteration or retrieval of deleted documents and emails. We at your service! We can assist you to investigate any unlawful, unauthorized, or unacceptable activity engineered on a computer network by an employee, a malware or a hacker.
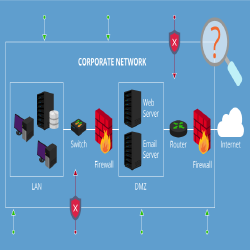
Penetration Testing
At Denfotech, we conduct cyber security assessment services on networks belonging to government, security agencies, corporate sector clients and tertiary institutions to assess the security of the network infrastructure against latest security vulnerabilities and exploits.
Our team of elite and industry experienced penetration testing professionals will assess the potential security vulnerabilities in your web, wireless and network infrastructure for immediate remediation against possible cyber-attacks.
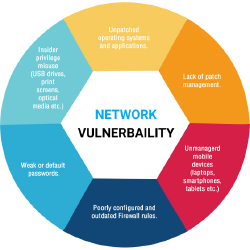
Vulnerability Assessment
Our vulnerability assessment services are designed to test your internal and external infrastructure against known security vulnerabilities and exposures.
We do these by thoroughly evaluating the security of an organization servers, security standards, network services, access points, firewalls, passwords, routers and switches for security flaws, misconfiguration and other vulnerabilities, and proceed as per agreement with our client.
You can check Common Vulnerabilities and Exposures (CVE) database for latest security vulnerabilities against your systems but implementing most them will be challenge to your organization – that is where we come in?

Incident Response
Denfotech offers Incident Response services to corporate organizations. We assist corporate bodies in establishing effective Computer Security Incident Response Team (CSIRT) to handle cyber security related incidents. We impact the knowledge to write sound corporate security policies as part of an organisation’s overall risk-management strategy to your CSIRT or IT Team. We also offer assistance to corporate organization desiring to build internal investigation capability to handle digital crime related issues involving employees.We also assist you to implement computer security incident response team by training your IT team to adhere to standard incident response methodologies when an incident occurs.
Vulnerability Assessment
Vulnerability Assessment is an authorized security assessment of an organisation IT infrastructure to discover existing vulnerabilities that can be exploited by a cyber criminal or disgruntled employee to achieve their criminal intent.
For an attack to be successful against your system or network, an attacker has to find a vulnerable system within your network with a known or unknown security vulnerability or configuration. A successful exploitation will involve leveraging security and hacking tools or techniques that connect to the vulnerable system for data exfiltration.
Penetration Testing
Penetration Testing is an authorized security assessment of an information system infrastructure against cyber-attack or security breach.
Vulnerability assessment and penetration testing are very similar in scope, except vulnerability assessment does not involved privilege escalation and exploitation of the target system. Penetration testing goes beyond vulnerability assessment by attempting to exploit the target system just like a cyber criminal or disgruntled employee will do.
Our Security Vulnerability Assessment Domains
|
|
Penetration Testing
As an industry leader in the information security assurance and electronic crime investigation business, Denfotech carries out three different types of security assessments in its business operations. Our penetration testing services is one of the three and uses proven testing methodologies to analyze, test and secure our clients networks from potential attacks and leaks. Denfotech uses the latest and security tools used by American and European government agencies to carry out security audit.
Types of Penetration Test or Vulnerability Assessment
Business organizations interested in comprehensive security assessments of their enterprises usually engages us to carry out the test on their premises internally or outside the business environment – usually through the internet. Based on client preference, Denfotech consultants carries out
Internal Penetration Testing or Vulnerability Assessment
External Penetration Testing or Vulnerability Assessment
Our Penetration Testing Approach
Denfotech consulting service practices are based on internationally accepted standards and are designed to provide your organization with a comprehensive assessment of your current cyber security needs and limitations, which may include security laps in enterprise policies, processes, procedures, practices, network, systems and application infrastructure.Whether Internal or External Penetration Testing, Denfotech uses different types of test approaches to conduct client security assessment
Zero Disclosure Test
This type of test is known as Black-Box Testing. In this approach, our penetration testing team comes in with no information about your system and must gather the relevant information as part of the testing process. We then proceed to simulate an attack on the system like a typical malicious hacker or cyber criminals would do without prior knowledge of the information system or infrastructure.
Partial Disclosure Test
This type of test is known as Grey-Box Testing. The penetration testing team is provided with little information that is relevant to start the testing process. The attack phase follows the initial information gathering and network reconnaissance phase. We rely on you to provide us with a little information that can help jumpstart the testing process. For example, supplying our team with various versions of the operating system deployed in your organization.
Full Disclosure Test
this type is known as White-Box Test. In this approach, our penetration testing team is provided with extensive information possible about the infrastructure to be tested. The test will replicate a certain attack that might be tried by an informed employee of an organization. The Information our team can be provided with includes Security policies, network diagrams and system configuration among others. This approach is typically used in our internal penetration test.
Our Penetration Testing Methodology
Denfotech uses a tried and proven testing methodology to execute the penetration test for its clients. The types and kind of security tools, scripts and code deployed for the testing depends on the nature and scope of the test. We have consistently outclassed our competitors using our proven methodology, expertise and professionalism
Pre-Engagement Activities
Phase 1 Scoping
Engagement Activities
Phase 2 Reconnaissance and Service Enumeration
Phase 3 Vulnerability Scanning and Analysis
Phase 4 Service Exploitation and Privilege Escalation
Phase 5 System Pivoting
Post Engagement Activities
Phase 6 Report Documentation and Presentation

Why should you partner with us to evaluate the security of your network infrastructure?
%
African networks vulnerable to cyber attacks
%
Very Affordable Cost - Lowest cost possible without comprising quality and tools.
%
80% of our team are certified and experienced technical cyber security and penetration testing experts!
%
Proven testimonials from our clients!

Why Choose Denfotech as your preferred cyber security partner in Chad?
 Our cyber security service practices are based on widely accepted standards and are designed to provide you with a comprehensive assessment of your organizations current security, which may include security laps in enterprise policies, processes, procedures, practices, networks, systems and applications.
Our cyber security service practices are based on widely accepted standards and are designed to provide you with a comprehensive assessment of your organizations current security, which may include security laps in enterprise policies, processes, procedures, practices, networks, systems and applications.
 Our Cyber Security team is led by a team of elite and certified cyber security professionals, who are among the best pioneers in cyber security in the country. We are certified by numerous vendors and security organization including Microsoft, VMware, Oracle, Cisco, EC-Council and many others.
Our Cyber Security team is led by a team of elite and certified cyber security professionals, who are among the best pioneers in cyber security in the country. We are certified by numerous vendors and security organization including Microsoft, VMware, Oracle, Cisco, EC-Council and many others.
Denfotech Cyber Security Certification Courses
Certified Wireless Security Engineer (CWiSE)
Course Description
Wireless security breaches are on the rise in every nation, unfortunately most IT administrators and Managers are not trained to effectively handle such tasks and most of them don’t even possess the skills to detect cyber intrusion or even detect interference that may be degrade the optimum performance of their wireless network. this course seeks to train participants to be effective wireless security administrators and security engineers.
Course Length:
20 Hours
Course Duration:
Bootcamp -> 4 days
Course Materials:
Wireless Security Ebooks (3 book)
Target Audience:
IT Auditors & System Administrators, IT Managers, IT Security Officers, Forensic and Network Auditors, Risk Managers, Law Enforcement Officers, Fraud Investigators, Cyber Security Researchers & Practitioners and Forensic Investigators
Course Objectives:
This course covers the three main areas of corporate wireless security:
participants are taken through an intensive wireless vulnerability assessment training by challenges them to break into wireless networks. participants will be taken various stages in wireless network attacks using wireless network attack tools. Participants will about the mindset of wireless hacker and how to out think them. They will acquire the knowledge and skills beyond ordinary hackers to design security for corporate wireless network.
A thorough and extensive training on the various wireless standards, best corporate wireless equipments, wireless network architecture best practices in wireless network deployment will be accomplished. Participants will use top rated wireless security assessment tools to analyze existing wireless to detect co-channel interference, overlapping, signal degradation and more. Participants will also learn to effectively defend corporate wireless networks against cyber-attacks
Many wireless administrators are not aware of wireless intrusion or how to investigate wireless attacks.h To enhance investigation in cases of cyber-attack against wireless network infrastructure, participants will learn to detect and investigate corporate wireless security intrusion and prepare report to management or police for further investigation.
Training Approach:
Presentation Methodology: PowerPoint slides with live demonstration of all concepts
Tools: Cutting-edge commercial and open source cyber security tools will be provided to all participants free of charge for hands-on exercises during training and for professional corporate security/investigative work.
Practical Sessions:
Participants will engage in Multiple hands-on and Intensive practical sessions with best the cyber/forensics tools used by FBI and other reputable corporate investigators / security agencies for investigating digital crimes committed in the work environment.
Fundamental Cyber Security Awareness Training
Course Description
organizations wants maximum security on information stored on their information systems, hence information security has therefore become an indispensable topic in the office. How many of your employees know about cyber security measures to protect their office documents and those on flash drives. Restricting your knowledge to antivirus defenses is not effective. Learn about the latest trend in cyber security and secure your documents now. This cyber security awareness course provides an in depth introduction to the field of Cyber Security. It serves as a very good introductory level course for those seeking a career in any information security related field as well as ordinary employees.
Course Length:
28 Hours
Course Duration:
Bootcamp -> 4 days
Course Materials:
Cyber Security ebooks (2 book)
Target Audience:
Ordinary Employees,information security enthusiasts, Senior and Junior Managers, IT Auditors & System Administrators, IT Managers, IT Security Officers, Forensic and Network Auditors, Risk Managers, Law Enforcement Officers,Cyber Security Researchers & Practitioners and Forensic Investigators
Course Objectives:
The courses covers various aspects of cyber security including:
- cyber security concepts and laws
- Mobile device security
- office cyber security threats and vulnerabilities ,
- information security principles,
- malware concepts (viruses, worms, trojan horses, rootkits, spyware, ad-words, ransomware)
- Anti-malware technologies (antivirus, rootkit revealers, anti-spyware)
- ethical hacking concepts and methodologies,
- Internet Security and web browser security,
- Network Security etc.
Training Approach:
Presentation Methodology: PowerPoint slides with live demonstration of all concepts
Tools: Cutting-edge commercial and open source cyber security tools will be provided to all participants free of charge for hands-on exercises during training and for professional corporate security/investigative work.
Practical Sessions:
Participants will engage in Multiple hands-on and Intensive practical sessions with best the cyber/forensics tools used by FBI and other reputable corporate investigators / security agencies for investigating digital crimes committed in the work environment.
Certified Cyber Security Engineer
Course Description
Administering security on Windows, Linux , Solaris Servers and network equipments is of extreme importance to IT administrators and professionals to safeguard corporate servers against security violation emanating from hackers, employees or malicious mobile codes such as viruses and worms. This course is design to maximize the knowledge of IT professionals administering corporate networks. This practical and hands-on course will equip your IT administrators with advance skills to detect internal and perimeter security threats against on the network and develop and implement security policies designed to secure the corporate networks against internal and external attacks.
Course Prerequisites
Participants must have knowledge windows domain controllers or Linux system administration.
Course Length:
28 Hours
Course Duration:
Bootcamp -> 4 days
Course Materials:
Cyber Security Ebooks (3 book)
Target Audience:
Network Engineers & System Administrators, IT Managers, IT Security Officers, Forensic and Network Auditors, Risk Managers, Fraud Investigators, Cyber Security Researchers & Practitioners and Forensic Investigators.
Course Objectives:
Prospective participant will acquire the knowledge and skillset to conduct network intelligence, expose network vulnerabilities and properly mitigate them. Administering and configuring security in Firewalls, Routers, Intrusion Detection Systems and Switches will also be highlight. Participants will monitor, inspect and analyze normal & malicious network traffic to detect security violation and security breaches.
We provide comprehensive system security training for management of different server roles (DHCP, DNS, and Active Directory etc.). Participants will acquire the knowledge and skills to design and implement security templates for restricting access to system services, registry and critical file system resources.
Participants will acquire the knowledge to apply security policies, access right management, and follow recommended guidelines to harden domain controllers against attacks and malicious codes. Participants will also learn to apply NTFS, Ext4 and Share permission to restrict access to corporate network resources as well as track any modification or deletion of files and folders on the corporate network.
Training Approach:
Presentation Methodology: PowerPoint slides with live demonstration of all concepts
Tools: Cutting-edge commercial and open source cyber security tools will be provided to all participants free of charge for hands-on exercises during training and for professional corporate security/investigative work.
Practical Sessions:
Participants will engage in Multiple hands-on and Intensive practical sessions with best the cyber/forensics tools used by FBI and other reputable corporate investigators / security agencies for investigating digital crimes committed in the work environment.
Certified Web Security Administrator Training
Course Description
Understanding web security, web server security, web application security, and web database security is very crucial in maintaining the security of online corporate servers against cyber-attacks. Attacks on web servers and websites are on the increase exponentially and many web administrators are not effectively train to handle this task. This course is designed to equip your web administrators with the knowledge, skills and techniques needed to combat cyber-attack on web servers and web services.
Course Length:
20 Hours
Course Duration:
Bootcamp -> 4 days
Course Materials:
Web Security e-books (3 ebooks)
Target Audience:
Web and SharePoint Administrators, IT Managers, IT Security Officers, Forensic and Network Auditors, Law Enforcement Officers, Cyber Security Researchers & Practitioners and Forensic Investigators
Course Objectives:
Participants will be equipped with the knowledge required to reduce web server attack and security guideline for controlling access to web servers, web sites, applications and server resources. Participant attending this class will be equipped with knowledge and skills to identify the source and identity of attackers who breach corporate web servers. Participants will analyze the security of web servers and the web applications running on them to check for vulnerabilities such as Cross Site Scripting (XSS) attacks, SQL injections, Cross Site Request Forgery, Security Misconfiguration, Parameter Tampering, broken authentication etc.
Training Approach:
Presentation Methodology: PowerPoint slides with live demonstration of all concepts
Tools: Cutting-edge commercial and open source cyber security tools will be provided to all participants free of charge for hands-on exercises during training and for professional corporate security/investigative work.
Practical Sessions:
Participants will engage in Multiple hands-on and Intensive practical sessions with best the cyber/forensics tools used by FBI and other reputable corporate investigators / security agencies for investigating digital crimes committed in the work environment.
Certified Digital Crime Analyst Training
Course Description
High-profile cases of corporate malfeasance and the need to preserve digital evidence has elevated digital forensics to an indispensable level in the 21st century organization. It has become an essential component of modern corporate IT security policy. This intensive instructor led course is designed to give a solid foundation in the theory and practice of essential digital forensic investigation methodologies and techniques. The course will enable corporate incident response team and cybercrime investigators follow solid forensic methodology, principles and techniques in gathering digital evidence from smartphones, computers, SIM Cards etc.
Course Length:
20 Hours
Course Duration:
Bootcamp -> 4 days
Course Materials:
Digital Forensics ebooks (3 book)
Target Audience:
IT Auditors & System Administrators, IT Managers, IT Security Officers, Forensic and Network Auditors, Risk Managers, Law Enforcement Officers, Fraud Investigators, Cyber Security Researchers & Practitioners and Forensic Investigators
Course Objectives:
This practical and hands-on course takes participant through digital crime scene investigation, seizing employee device, image acquisition, image analysis, preservation of evidence and reporting, recovering of deleted files and hidden incriminating evidence in video, audio and pictures. Participants will also learn how criminals and government security agencies such as the FBI and CIA encrypt and decrypt sensitive data, detect alteration to corporate documents, and use tools to hide sensitive documents in pictures, mp3 and videos.
Training Approach:
Presentation Methodology: PowerPoint slides with live demonstration of all concepts
Tools: Cutting-edge commercial and open source cyber security tools will be provided to all participants free of charge for hands-on exercises during training and for professional corporate security/investigative work.
Practical Sessions:
Participants will engage in Multiple hands-on and Intensive practical sessions with best the cyber/forensics tools used by FBI and other reputable corporate investigators / security agencies for investigating digital crimes committed in the work environment.
Certified Network Vulnerability Analyst Training
Course Description
Only trusted IT professionals in an organization should be allowed to undergo this training. The knowledge to be acquired from this training can be use for evil purposes. This course has been designed to equip IT Professionals with the same knowledge used by sophisticated hackers to penetrate highly protected corporate information systems. The course however goes beyond normal ethical hacking course by turning your IT professional into sophisticated professional capable penetrating any network to access it security. Prospective participants will acquire advance knowledge and skills to conduct vulnerability assessment on corporate networks. Participants will learn to discover security vulnerabilities and use exploits to penetrate information systems, Privilege escalation, Disabling Antiviruses and Bypassing firewalls will be covered during the training. Securing corporate information systems against cyber-attacks and security vulnerabilities will highlighted at the end of the training.
Course Length:
20 Hours
Course Duration:
Bootcamp -> 4 days
Course Materials:
Digital Forensics Ebooks (3 book)
Target Audience:
IT Auditors & System Administrators, IT Managers, IT Security Officers, Forensic and Network Auditors, Risk Managers, Law Enforcement Officers, Cyber Security Researchers & Practitioners and Forensic Investigators
Course Objectives:
- Penetration Testing and Network Vulnerability Assessments Introduction
- Network Vulnerability Testing Methodologies
- Phases in Network Vulnerability Assessments
- Corporate Network Scanning Stages and Target Reconnaissance
- Vulnerability Assessment Execution, Exploitation and Pivoting
- Results Analysis and Reporting to Management
- Vulnerability Remediation
Training Approach:
Presentation Methodology: PowerPoint slides with live demonstration of all concepts
Tools: Cutting-edge commercial and open source cyber security tools will be provided to all participants free of charge for hands-on exercises during training and for professional corporate security/investigative work.
Practical Sessions:
Participants will engage in Multiple hands-on and Intensive practical sessions with best the cyber/forensics tools used by FBI and other reputable corporate investigators / security agencies for investigating digital crimes committed in the work environment.
Why Choose Denfotech Training?
Our training are very intensive because of the numerous practical sessions and hands-on exercises involved. They are designed to maximize the technical knowledge of your IT officers and managers to effectively:
Defend your corporate network against cyber attacks and security breaches.
Conduct vulnerability assessment of your corporate network by performing penetration testing.
Investigative corporate security breaches, intrusion and violation by sophisticated hackers or employees.
Certificates upon completion of a course.
Interested in any of our training?
Please fill the contact form above specifying the course of interest to your organisation!
About Us
Works & Testimonials
What We Do
Contact Us
Location Address
145 Rue no. 5447, Quartier Dembe, 7th Arrondissement, Ndjamena.
Telephone
+233 570 716622 (WhatsApp )
